How Hackers Shape Human Actions through Social Engineering
The world of cybersecurity, one of the most effective and widespread threats comes not from sophisticated algorithms or inaccessible firewalls but from something far more unpredictable and malleable is human behavior. Social engineering is a form of cyber-attack that exploits the very essence of human nature, relying on psychological manipulation rather than code or technical vulnerabilities.
The Basics of Social Engineering
At its core, social engineering is the art of manipulating individuals into exposing confidential information, clicking on malicious links, or performing actions that they otherwise would not have. It preys on common human traits such as trust, curiosity, and fear, and it can take many forms.
Let’s explore some of the most common tactics used by social engineers:
Phishing:

Phishing is perhaps the most well-known form of social engineering. It involves sending seemingly legitimate emails or messages to trick recipients into revealing sensitive information or downloading malicious software. These messages often appear to come from trusted sources, such as banks or well-known companies, and urge the recipient to take immediate action.
Pretexting:
Pretexting is a technique that involves creating a pretext to manipulate individuals into revealing information. For example, a hacker might impersonate an IT technician and call an employee, claiming to need their login credentials for a system update.
Baiting:
Baiting relies on enticing victims with something they desire, such as a free download, to lure them into clicking on a malicious link or downloading malware. It preys on curiosity and the desire for something for nothing.
Tailgating:

Tailgating, or piggybacking, involves physically following an authorized person into a restricted area by appearing to be someone with a legitimate reason to enter. This technique exploits trust and social norms.
Quid Pro Quo Attacks
Quid pro quo attacks are a well-known form of social engineering, where hackers employ a give-and-take approach. As example, offering free services or goods in exchange for personal details. These tactics are frequently used to breach systems and networks, aiming to steal personal and financial data.
Scareware Attacks
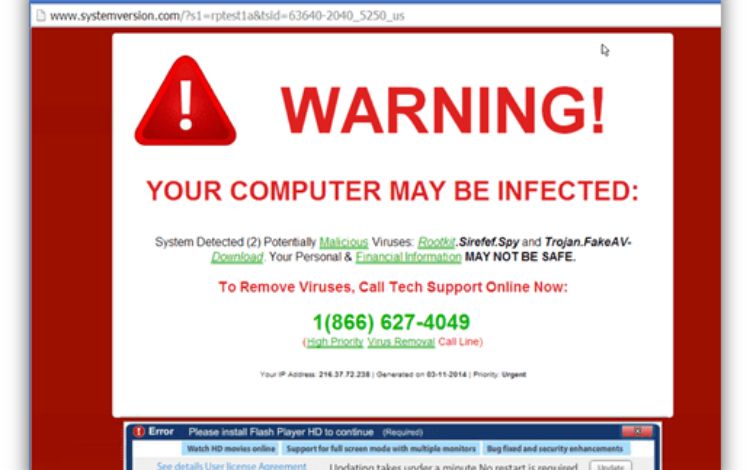
Scareware attacks utilize malicious software to deceive users installing a specific application or file. The goal is to induce fear, making users believe their computer has been compromised and urgently requires fixing. Detecting these social engineering attacks can be challenging, potentially resulting in significant financial losses and data exposure.
Watering Hole Attacks
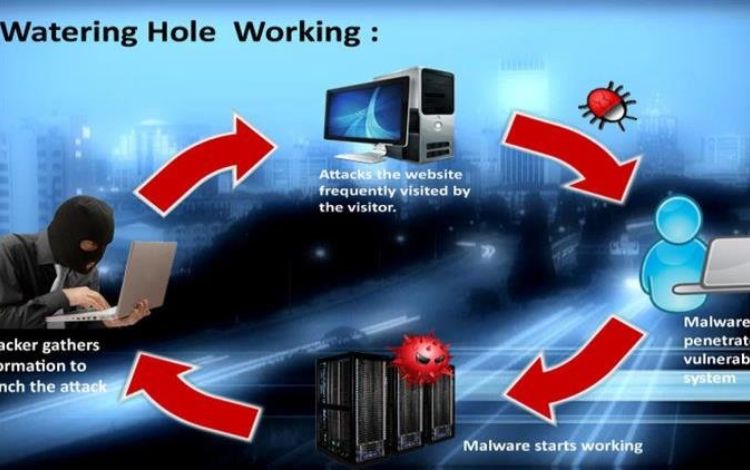
Watering hole attacks target specific groups of individuals by exploiting commonly visited websites. Hackers inject these websites with malicious code, allowing them to extract information from unsuspecting users which is challenging to identify and defend.
The Psychology Behind Social Engineering
Trust-
Humans are naturally inclined to trust others, especially when the person appears to be in a position of authority. Social engineers often exploit this trust by posing as someone trustworthy, such as a colleague, supervisor, or technical support representative.
Fear and Urgency-
Creating a sense of urgency or fear can override rational thinking and lead individuals to act impulsively. Social engineers often use tactics like threatening to shut down an account to manipulate victims into taking immediate action.
Curiosity-
By exploiting people’s natural curiosity, social engineers create scenarios or offer incentives that pique individuals’ interest and entice them into taking risky actions, such as clicking on a link or opening an attachment.
Reciprocity-
The principle of reciprocity states that when someone does something for us, we feel an obligation to return the favor. Social engineers use this by offering something small (like a free download or assistance) to establish a psychological debt that victims feel compelled to repay.
Social engineering attacks can have severe consequences, both for individuals and organizations. Like,
- Data Breaches: Social engineering attacks can lead to the unauthorized access and theft of sensitive data, including personal information, financial records, intellectual property, and trade secrets.
- Financial Loss: Victims of social engineering attacks may suffer financial losses through fraudulent transactions, unauthorized access to bank accounts, or theft of funds.
- Identity Theft: Social engineers often target personal information, which can result in victims facing credit card fraud, unauthorized loans, and damage to their credit scores.
- Reputation Damage: Individuals and organizations that fall victim to social engineering attacks may experience significant damage to their reputation. This can lead to a loss of trust from customers, clients, or peers, and can be challenging to recover from.
- Operational Downfall: Social engineering attacks can disrupt normal business operations. For example, a successful phishing attack that compromises employee accounts may lead to downtime, loss of productivity, and increased IT support costs.
- Psychological Impact: Victims of social engineering attacks often experience stress, anxiety, further exploitation and a sense of violation, leading to long-term psychological consequences.
- Strain on Relationships: In personal contexts, social engineering attacks can strain relationships if the victim’s personal information is used to target friends, family, or colleagues.
- Continued Vulnerability: Once an attacker has obtained certain information or established trust, they may continue to exploit it for ongoing gain.
Real-World Examples
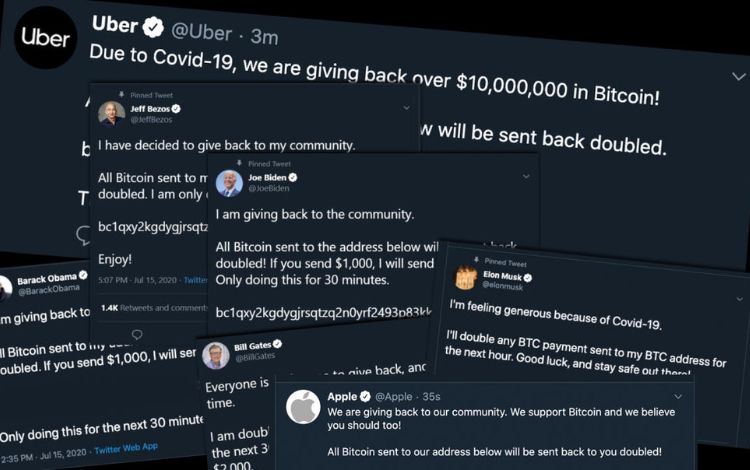
The Twitter Bitcoin Scam
In July 2020, a massive Twitter breach saw high-profile accounts like those of Elon Musk, Barack Obama, Bill Gates, Apple compromised. Hackers used social engineering tactics to trick Twitter employees into providing access to internal tools, allowing them to post cryptocurrency scams based on the urgency and trust associated with these high-profile accounts.
The CEO Fraud Scam
CEO fraud is a form of pretexting where a hacker impersonates a company’s CEO/higher authority to target employees in the finance department and request large wire transfers to external accounts. In 2015, Mattel fell victim to such a scam, losing over $3 million.
The USB Drop Attack
In a physical social engineering attack, an attacker might drop a seemingly innocuous USB drive in a parking lot. Curiosity often gets the best of someone who finds it, and they plug it into their computer that contains malware that infiltrates their system.
Protecting Against Social Engineering
- Security Training: Regular security awareness training can educate employees about the dangers of social engineering and teach them how to recognize and respond to suspicious requests or messages.
- Verification Protocols: Implement robust verification protocols for sensitive actions, such as fund transfers or account access changes. Always verify requests through a separate communication channel.
- Strong Authentication: Use strong authentication methods, such as multi-factor authentication (MFA), to add an extra layer of security to accounts and systems.
- Cybersecurity Tools: Utilize cybersecurity tools like email filtering, intrusion detection systems, and endpoint protection to help detect and mitigate social engineering attacks.
- Multi-Factor Authentication: Implement MFA wherever possible to add an additional layer of security, even if an attacker has obtained login credentials.
- Cybersecurity Policies: Establish robust cybersecurity policies that govern the sharing of sensitive information and the verification of requests for such information.
- Regular Updates: Keep software, operating systems, and security software up to date to minimize vulnerabilities that social engineers may exploit.
- Incident Response Plans: Develop and test incident response plans so that, in the event of a successful social engineering attack, organizations can minimize damage and recover quickly.
- Verify Before Trusting: Always verify the identity of individuals making requests for sensitive information, especially when they seem unusual.
In conclusion, the art of social engineering demonstrates that the human factor is often the weakest link in cybersecurity. By understanding the psychology behind these attacks and implementing proactive measures, individuals and organizations can better defend against the ever-evolving tactics employed by hackers. Remember, the first line of defense against social engineering is awareness and skepticism—always think twice before clicking that link or sharing sensitive information.
Writer
Fariha Zannat
Intern, Content Writing Department
Requin BD





Write a Comment